Drive cloning — Larger to smaller hard drive (or SSD) using Clonezilla
Requirements:
Ability to use Clonezilla
Ability to use Gparted
Ability to do simple arithmetic (remember arithmetic?)
Procedure:
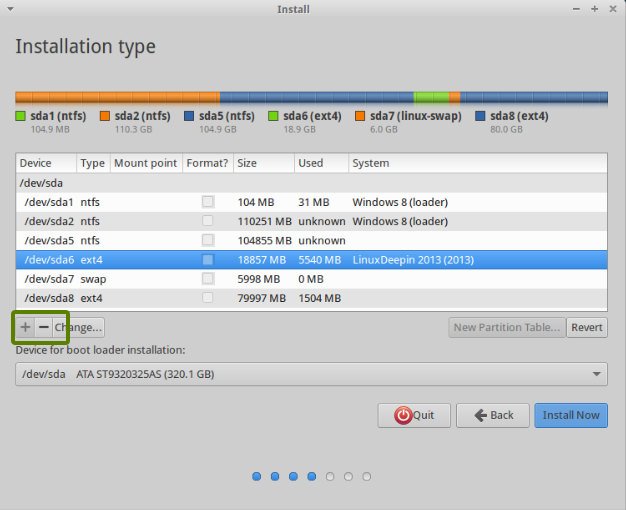
Using Clonezilla, I’ve always heard you can only clone a hard drive to a drive that is the same size or bigger. Not so. I just cloned a 250 GB to a 240 GB, and I suspect this method will work for any size drive difference. The only requirement is that the sum of the size of the partitions on the source drive must not be larger than the total size of the target drive. To make this the case, it will probably be necessary to resize the partitions on the source drive using Gparted. Of course, be aware that Gparted can only reduce the size of any partition to no smaller than the amount of data that it holds (known as “used space”).
In my case, the source drive is 250 GB with four partitions – one for Windows XP, one for Windows 7, one for Linux, and one for Linux swap. This is a triple boot PC using Grub2 as the initial boot manager for Linux, and Windows 7 as the secondary boot manager for both XP and 7. So this was a rather unusual boot scenario that I needed Clonezilla to clone correctly.
The target drive was a 240 GB SSD, which should be blank (unpartitioned). If it is not blank, that’s fine, as everything (data and partitions) will be erased by the cloning process automatically by Clonezilla. It will warn you about this several times. So if the target drive has anything on it you want to save, save it before starting the cloning process.
The target drive is 10 GB smaller than the source drive, so the first thing I needed to do was reduce the size of one or more partitions on the source drive by a total of 10+ GB using Gparted. I had over 30 GB of free space on the Windows 7 partition, so I reduced its partition size by 10 GB. I also deleted the 4 GB Linux swap partition after I reconfigured Linux to use a swap file instead of a swap partition, which meant I reduced the size of my partitions by 14 GB overall. Finally, also using Gparted on the source drive, I then moved all the unallocated space to the end of the drive. In my case, to move the unallocated space to the end, I simply moved the Linux partition “to the left” to immediately follow the Windows 7 partition. This is important, as you want your partitions to be contiguous from the beginning of the source drive so that they will all fit on the smaller target drive. The unallocated space, which is now all at the end of the source drive, will be ignored by Clonezilla, as if it isn’t even there. In that way, the source drive appears to be smaller than the target drive to Clonezilla.
Once the source drive is configured like this, it is time to have both source and target drives attached to the computer and boot into Clonezilla from CD (or USB). We are going to do a drive-to-drive copy, using expert mode.

We choose expert mode so we can select the -icds option when prompted, in addition to keeping all the pre-set default options.

Finally, when prompted on how to handle cloning the partition table, choose “Use the partition table from the source drive.”

Pay attention to the warnings Clonezilla gives you about erasing the target drive, verifying that the drive it will be erasing is indeed your target drive and not the source drive. Then let Clonezilla do the cloning, and if there are no errors reported due to bad sectors or other unforeseen problems, you should end up with a bootable clone of your once-larger source drive on the smaller target drive. It worked for me.
Image source